Keep calm and scan your vulnerabilities




Going Beyond Automation for Accurate Vulnerability Assessment of Your Infrastructure and Applications!
We believe in taking a hands-on approach to ensure precise vulnerability scanning. Our expert team goes the extra mile to provide you with a comprehensive evaluation. Here’s how we achieve accuracy:
- Personalized Training for Scanners. We fine-tune our scanners to capture all critical functionalities while excluding irrelevant ones. We configure scanners to work appropriately with or without authentication, ensuring they accurately assess security based on policies and standard requirements.
- Thorough Double-Check. To minimize false negatives, we conduct a thorough double-check by running a second scanner. This additional step adds an extra layer of scrutiny to ensure that no vulnerabilities are missed.
- Comprehensive Report. Our final report is a culmination of insights from all scanners, combined with our expert analysis. This comprehensive approach provides you with a holistic view of the vulnerabilities present in your infrastructure and applications.
Testing vectors
Our analysis encompasses an in-depth understanding of potential threats that your assets may face, whether it's from external hackers, insiders, guests, remote access partners, any other potential risks or their combination:
Enhance your company's vulnerability management process with your own top vulnerability scanners.
Acunetix
Improve the security of your WEB applications with the Acunetix Vulnerability Scanner – the most mature and fastest vulnerability scanning tool available known for its very low false-positive rate . Acunetix is not just a web vulnerability scanner, but a comprehensive web application security testing solution. With built-in vulnerability assessment and management capabilities, as well as seamless integration options with leading software development tools, Acunetix significantly enhances your cybersecurity posture.
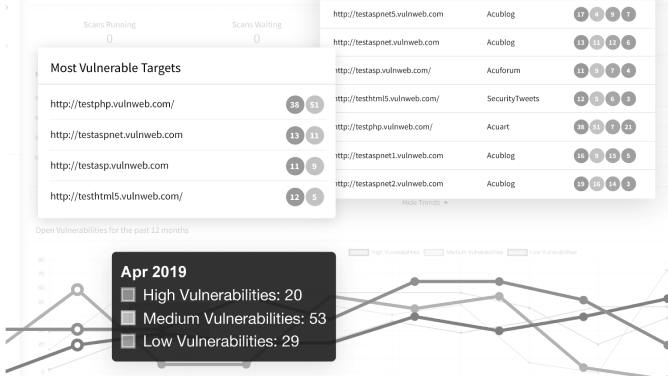
Rapid 7

Rapid 7
Reduce your exposure to threats and effectively manage vulnerabilities with Rapid7’s on-premise solution, Nexpose. By continuously assessing and responding to changes in your environment, Nexpose helps you prioritize risks across vulnerabilities, configurations, and controls in real-time.
In today’s dynamic threat landscape, your attack surface is constantly evolving, and adversaries are becoming more agile than ever. With Nexpose, you can gain the confidence to understand your attack surface, focus on critical areas, and achieve better security outcomes.
Nexpose ensures compliance with industry standards such as PCI DSS, NERC CIP, FISMA (USGCB/FDCC), HIPAA/HITECH, Top 20 CSC, DISA STIGS, and CIS for risk, vulnerability, and configuration management. Unlike other solutions that may burden your network with multiple scans, Nexpose offers fast, unified security and compliance assessments that enhance the performance of your security program, providing a comprehensive view of your risk and compliance posture.
For more advanced capabilities, such as Remediation Workflow and the Rapid7 Insight Agent, explore InsightVM, the platform-based vulnerability management software.

Rapid 7

Rapid 7

Team portfolio










Our certificates










Sometimes there are questions...
Why do I need vulnerability scanning?
Vulnerability scanning is essential for maintaining the security of your systems and applications. It helps identify weaknesses and potential entry points that could be exploited by attackers. By regularly conducting vulnerability scans, you can:
- Identify Security Weaknesses: Scans detect vulnerabilities in your network, operating systems, and applications, providing valuable insights into potential security risks. Regular scanning allows you to monitor and improve your security over time, reducing the risk of successful cyber attacks.
- Stay Compliant: Many industry standards and regulations, such as PCI DSS, HIPAA, and ISO 27001, require regular vulnerability assessments. Scanning helps you meet these compliance requirements.
- Protect Your Reputation: By proactively addressing vulnerabilities, you demonstrate your commitment to security and protect your reputation from potential breaches.
How secure is the vulnerability scanning procedure for our environment?
Our goal isn’t to give your systems a bad day with a Denial of Service, but it’s important to understand that we actively attempt to push the systems beyond their usual functioning boundaries.
Now, if we’re venturing into the realm of production environments and dealing with critical systems, fear not! We have a bag of tricks to keep things in check:
- Risky business like vulnerability scanning will only happen aftermutually agreeingwith you on the perfect timing. You can choose a maintenance window, for example, during weekends or nighttime, to minimize the risk for your customers.
- Manual checks will be handled with the grace of a tightrope walker, and our scanners willbe configured totiptoe around your systems like a ninja on a moonlit mission.
- We will establish an incident escalation procedure in coordination with you, ensuring that you are prepared to respond promptly if any incidents occur.It’s rare, but let’s face it, life is full of surprises.
- And don’t forget your system backups, always better to have them on standby.
Another option is testing in an environment identical to the production environment.
What tools do we use?
We utilize paid tools for vulnerability scanning:
- Acunetix & BurpSuite for Web application scanning.
- Nexpose & Nessus for network scanning.
To minimize false negatives, we conduct a thorough double-check by running a second scanner. This additional step adds an extra layer of scrutiny to ensure that no vulnerabilities are missed.
Do you perform a fully automated vulnerability scanning?
The dream of any professional is to press a button, sit back in their chair, sip coffee, and wait for the scanner to do all the work… but that’s not how it works.
Human involvement is necessary to:
- Perform a double-check using another scanner to ensure accuracy.
- Interpret and consolidate results from multiple scanners into a single report with recommendations.
- Train the scanner to authenticate and maintain a live session within the application; otherwise, you would be testing the authentication form rather test the application itself.
- Equip the scanner with maximum knowledge about application functionality, as it cannot fully achieve this on its own.
- Implement restrictions on the scanner to prevent harmful actions such as data deletion or modification of critical settings.
Do standards require vulnerability scanning?
PCI DSS (Payment Card Industry Data Security Standard)
Requirement 11.2: Perform internal and external network vulnerability scans at least quarterly and after any significant change in the network.
“Regularly scanning your network for vulnerabilities is essential to maintain the security of payment card data.”
ISO 27001 (International Organization for Standardization)
Control A.12.6.1: Management of technical vulnerabilities.
“Organizations shall regularly perform technical vulnerability assessments to identify vulnerabilities and take appropriate actions to address them.”
NIST SP 800-53 (National Institute of Standards and Technology)
CM-8 (Information System Component Inventory): Conduct periodic scans of the information system and real-time scans of files from external sources.
“Periodic vulnerability scanning helps identify and address potential security weaknesses in the information system.”
CIS (Center for Internet Security) Controls
Control 3: Continuous Vulnerability Management.
“Regularly scanning for vulnerabilities is crucial to ensure the ongoing security of your systems and data.”
OWASP (Open Web Application Security Project) Top 10
A9: Using Components with Known Vulnerabilities.
“Regularly scanning for and addressing vulnerabilities in third-party components helps prevent security breaches.”
HIPAA (Health Insurance Portability and Accountability Act)
45 CFR 164.308(a)(1)(ii)(B): Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information.
“Regular vulnerability assessments are necessary to protect sensitive health information from potential threats.”
We appreciate your request.
Wait for the answer..
It will come.
I'll be waiting...